Cyber Security Solutions

Need Help?
Next-Generation Firewall
Modern attacks require Next-Generation protection.
A Next-Generation Firewall unifies deep-packet inspection, application awareness, user identity, and real-time threat intelligence in one platform. It evaluates every session in context deciding, within micro-seconds, whether to allow, monitor, or block traffic, so your organization stays secure without sacrificing performance.

Benefits
-
Crystal-clear visibility – Application & User-level analytics show who did what, instantly.
-
Proactive breach prevention – Integrated intrusion-prevention, sandboxing, and AI-driven malware analysis.
-
Regulatory compliance – Audit-ready reports for PCI-DSS, HIPAA, GDPR, ISO 27001, and RBI.
-
Consistent high performance – Hardware acceleration maintains throughput even with SSL/TLS inspection.
-
Automated response workflows – Integrates with SIEM/SOAR to quarantine endpoints or block IPs in real time.
-
Scalable high availability – Active clustering and geo-redundant architecture ensure continuity.
-
Integrated threat protection – IPS, antivirus, and URL filtering for layered defense.
-
Behavioral analysis – Detects zero‑day and insider threats missed by signatures.
Endpoint Detection & Response (EDR) / Extended Detection & Response (XDR)
Threats move fast, EDR & XDR move faster.
EDR hunts for malicious activity on every endpoint, while XDR correlates data across endpoints, network, cloud, identity, and email for unified, high-fidelity detection and automated response.

Benefits
-
Complete endpoint visibility – Kernel-level sensors capture processes, memory, and registry changes in real time.
-
Cross-domain correlation – XDR stitches telemetry to reveal multi-stage attacks.
-
Automated containment – One-click or policy-driven isolation, kill-process, and rollback.
-
AI-powered analytics – Behavioral models detect zero-day and file-less attacks.
-
Ransomware rollback – Volume Shadow Copy integration restores encrypted files in seconds.
Managed Detection & Response (MDR)
Elite threat hunting on tap, no hiring required.
MDR blends always-on monitoring, advanced analytics, and human experts to detect, investigate, and eliminate threats across your environment 24 × 7.
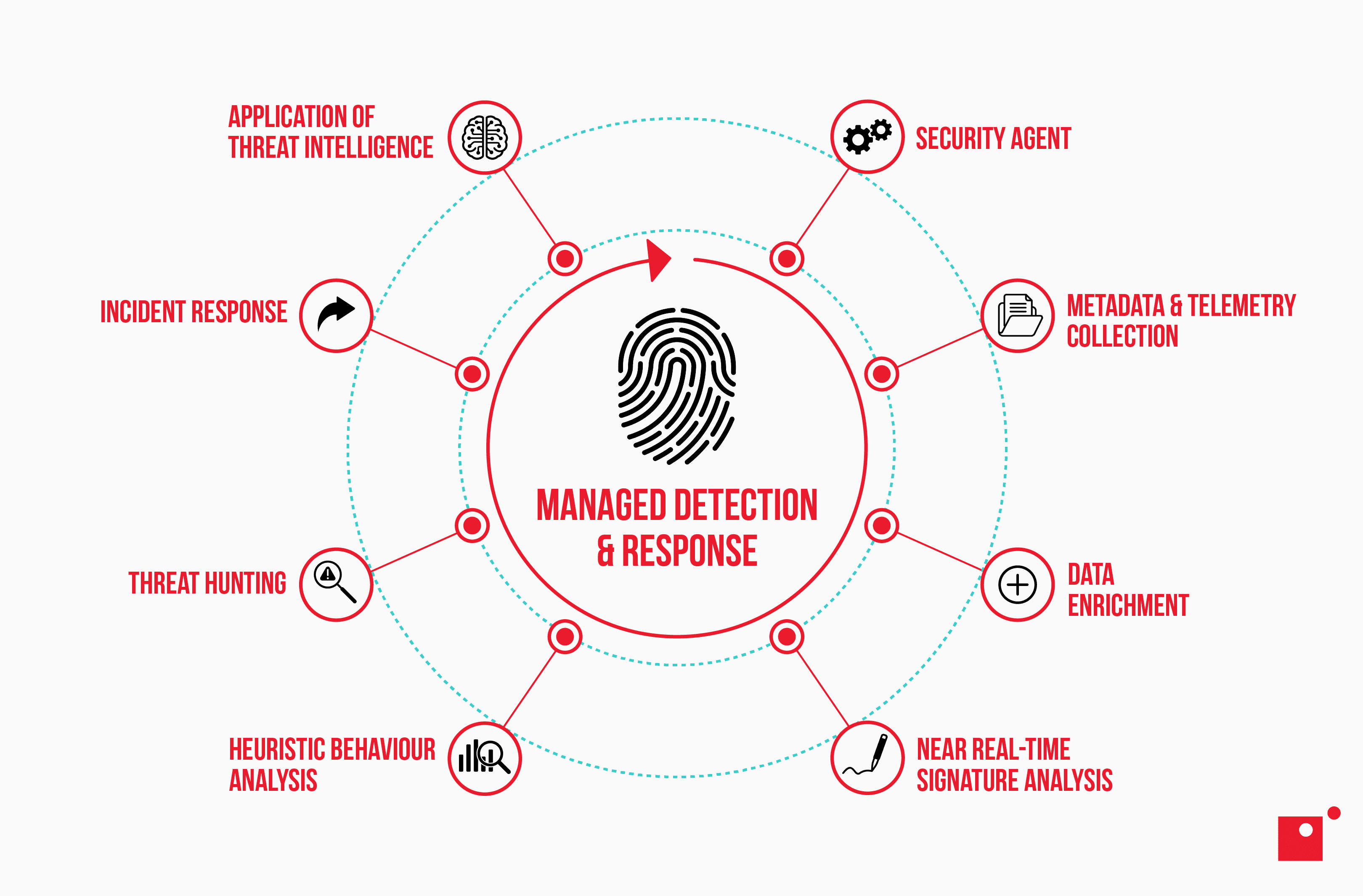
Benefits
-
24 × 7 hunting & triage – Certified analysts investigate anomalies round the clock.
-
Rapid incident response – Average time-to-contain under 15 minutes.
-
Dedicated Customer Success Manager – Monthly threat-intel and risk posture reviews.
-
Threat-intel enrichment – Mapped to MITRE ATT&CK for contextual alerts.
Zero Trust Network Access (ZTNA)
Never trust, always verify - every connection, every time.
ZTNA replaces legacy VPNs with identity-, device-, and context-aware micro-tunnels that grant access only to specific applications, not the entire network.
Benefits
-
Application-level segmentation – Users only access authorized apps.
-
Dynamic risk scoring – Session trust adapts to device, location, and behavior.
-
Invisible infrastructure – Apps stay dark to internet scans and DDoS.
-
Seamless user experience – Single-packet inspection and SSO for smooth access.
-
Hybrid & multi-cloud ready – Consistent policies across on-prem and cloud.
Why Leading Brands Choose Trace
24×7 SOC & Seamless Support Continuous monitoring, rapid incident response, and proactive tuning by certified analysts.
Multi‑vendor, Certified Expertise With 40+ Global OEM Partnerships, we are bringing you future-proof solutions matched to your exact needs.
20 Years of Leadership Proven security and networking solutions for top institutions and data centers across South India.
Customer‑First, Value‑Driven Right-sized solutions that deliver maximum protection at the lowest total cost of ownership.
Local Presence & Rapid Support Engineers in Hyderabad, Bengaluru, Chennai, Vijayawada, and Vizag for quick onsite help.
ISO 27001‑Certified Stringent change management and documentation aligned with global best practices.
Proven Deployment Framework Assess → Design → Deploy → Optimize → Support. Minimizing downtime and boosting ROI.
Flexible Commercial Models CapEx, OpEx, and MSSP pricing aligned with business cash-flow goals.