Cyber Security Solutions

Need Help?
Data Loss Prevention (DLP)
Your data is your business, keep it where it belongs.
DLP identifies, classifies, and protects sensitive data in motion, at rest, and in use, automatically blocking unauthorized sharing or exfiltration.

Benefits
-
Deep content inspection – OCR and fingerprinting detect PII, PHI, and IP inside images and zip files.
-
Adaptive policies – User behavior, destination, and data type determine block, encrypt, or allow.
-
Cloud & endpoint coverage – Enforce identical controls across SaaS, email, and USB devices.
-
Granular incident workflow – Real-time prompts reduce leaks; forensic logs ease investigations.
-
Regulatory templates – Pre-built rulesets for GDPR, RBI, CCPA, PCI-DSS, and HIPAA.
Email Security
Stop the phishing flood before it hits the inbox.
Multi-layer email security combines AI-driven phishing detection, URL rewriting, sandboxing, and DMARC enforcement to block BEC and malware.

Benefits
-
AI & NLP – Detects impersonation, look-alike domains, and social-engineering attacks.
-
Attachment sandboxing – Detonates suspicious files in secure VMs.
-
Time-of-click URL protection – Rewrites links and rescans on click to catch delayed payload swaps.
-
Integrated awareness training – Auto-phish simulation lowers click-rates by 60%.
-
Inline encryption & DLP – Protects sensitive outbound emails without user friction.
Asset & Patch Management
You can’t patch what you can’t see, gain both insight and action.
Continuous asset discovery, vulnerability assessment, and automated patch deployment for OS, third-party apps, and firmware across endpoints and servers.
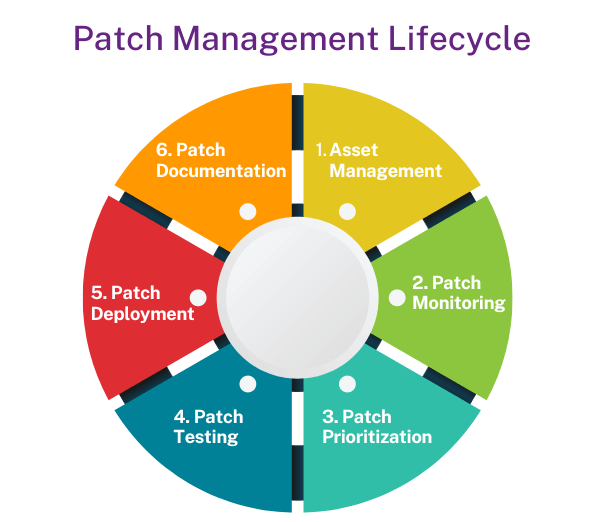
Benefits
-
Unified asset inventory – Real-time CMDB with hardware, software, and lifecycle status.
-
Risk-based prioritization – CVSS scoring and exploit intelligence for focused remediation.
-
One-click patch rollouts – Schedule, stage, and rollback with safety nets.
-
Cross-platform coverage – Windows, macOS, Linux, and virtual infrastructure in one console.
-
Compliance dashboards – Prove patch SLAs for ISO 27001, RBI, and CIS benchmarks.
Backup & Recovery Solutions
Because downtime is not an option.
End-to-end data protection with image-based, incremental, and cloud-replicated backups featuring instant restore and ransomware-proof immutability.

Benefits
-
Any-to-any recovery – Bare-metal, VM, or cloud restores to dissimilar hardware.
-
Immutable storage – Write-once object locking thwarts ransomware encryption.
-
15-minute RPO / near-zero RTO – Continuous protection and instant VM boot.
-
Multi-cloud replication – AWS, Azure, and on-prem targets for geo-redundancy.
-
Automated DR testing – Non-disruptive failover drills with compliance reports.
Why Leading Brands Choose Trace
24×7 SOC & Seamless Support Continuous monitoring, rapid incident response, and proactive tuning by certified analysts.
Multi‑vendor, Certified Expertise With 40+ Global OEM Partnerships, we are bringing you future-proof solutions matched to your exact needs.
20 Years of Leadership Proven security and networking solutions for top institutions and data centers across South India.
Customer‑First, Value‑Driven Right-sized solutions that deliver maximum protection at the lowest total cost of ownership.
Local Presence & Rapid Support Engineers in Hyderabad, Bengaluru, Chennai, Vijayawada, and Vizag for quick onsite help.
ISO 27001‑Certified Stringent change management and documentation aligned with global best practices.
Proven Deployment Framework Assess → Design → Deploy → Optimize → Support. Minimizing downtime and boosting ROI.
Flexible Commercial Models CapEx, OpEx, and MSSP pricing aligned with business cash-flow goals.